Kekistani Code Talkers
Understandably Irregular, Totally Misunderstood ... Entirely Expected
Shadilay!
Welcome to another wild adventure down the rabbit hole less traveled. I hope you brought your special cryptographic key. If not, whatever you do, do not panic! Instructions on how to obtain another key will be presented below.
“A key for what?” you are likely asking. Well, I believe this key unlocks the door of all doors, mentioned by Q in drop #269. (Note, Q uses parenthetical clarification to highlight that the door of all doors is informational in nature.)
To re-state this, the key unlocks information.
“What information does this key unlock?” you’ll logically ask next.
Well, this key unlocks important details about the root cause and solution to our current tyranny. Also, while I won’t discuss the ‘stone’ here, note that Q defines it as the [capability of projecting power].
Softwar vibes!
Let’s start today’s journey by establishing a common foundation to help ensure we’re all on the same page.
To do this, I’ll ask several questions alongside key data points, provide a handful of resources containing important background information and analyses, and walk through some basic definitions and examples. Afterwards, we’ll review several case studies in history that support the unique conclusions I’ll draw at the end.
Let’s GO!
Questions and Key Data Points
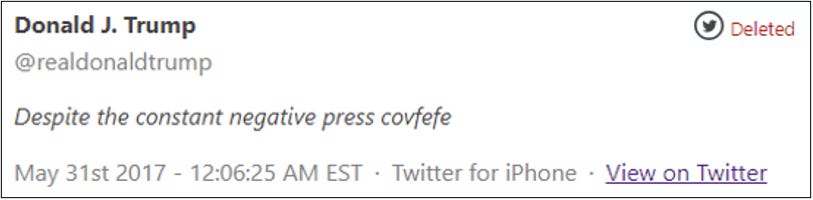
First, was one of the most epic “Stable Genius” moves by President Trump when he Tweeted about Covfefe on 5/31/2017?
Second, why did Trump delete this Tweet, but then ask who could figure out its true meaning 6 hours and 3 minutes later?
Third, why did Trump challenge the Tweet being labeled a “mistweet” over 2 years later, and why does Trump (and others) suggest Covfefe is something with much deeper meaning?
Lastly, is Covfefe a cryptographic key, and if so, what information does it allow access to, or what puzzle does it solve?
Resources
Below are several short articles GMONEY and I have published that contain important background information and analyses:
While you don’t have to read them…
The Basics
In simple terms, a cryptographic key allows someone to either create (encrypt) or solve (decrypt) a cryptographic puzzle.
You can think of the key as a Rosetta Stone or translator that allows people to play a game of hiding and attempting to discover secrets. Today, the game can be analog, digital, or hybrid.
Modern encryption methodologies also provide one way encryption (such as secure hashing algorithms).
Therefore, encryption in many forms has been used throughout time to protect information from unauthorized access during storage and transmission. Due to the competitive and strategic advantages protected information can provide, encryption has served as one of the most powerful weapons of information warfare throughout history.
Here is Sun Tzu discussing information warfare from the perspective of an entirely analog battlefield:
Now, let’s look at some definitions.
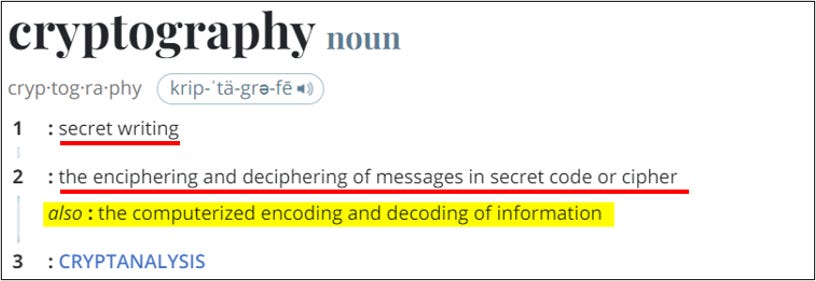
First up, the definition of cryptography:
I’ll emphasize:
Cryptography deals with secret writing and messages.
Enciphering, encoding, and encryption are synonymous terms, reflecting different areas of encryption as a broader study (same with “de” terms).
Codes and ciphers are cryptographic puzzles.
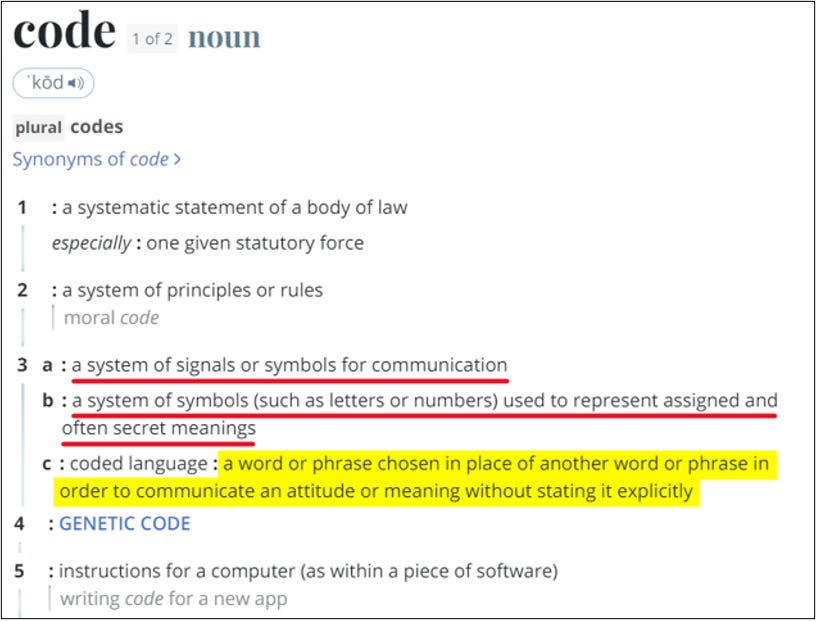
Let’s pull on that last thread and look at the definitions of code and cipher:
I’ll emphasize:
Codes are systems of signals or symbols.
Symbols can be letters, numbers, shapes, etc.
Symbols represent assigned (abstract) and often secret meanings.
Codes are for communication.
I’ll emphasize:
Ciphers transform data to conceal meaning.
Ciphers cannot be decoded without the key.
Ciphers can be any combination of symbols, letters, numbers, etc.
Ultimately, codes and ciphers come in all shapes and sizes. The examples are endless, due to the uniqueness of the human brain and its ability to think abstractly. Humans constantly develop systems that ascribe abstract meaning to different symbols. Then, they expend massive amounts of energy to keep the code or cipher a secret, or convince others to adopt its use.
Codes and ciphers are often an important factor in a civilization’s rise, longevity, and fall; therefore, codes and ciphers are heavily researched and used by a civilization’s military.
The SHA-2 family consists of six hash functions, one of which is SHA-256 (which is the algorithm used for mining/unlocking Bitcoin.)
I don’t believe it’s a coincidence that Q used cryptographic puzzles. The cryptographic nature of the drops has left Anons worldwide trying to “decode” everything imaginable since day one (right, wrong, or indifferent).
Today, I’ll focus on one of Q’s earliest uses of cryptographic puzzles.
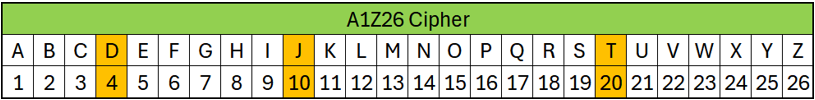
In drop #35, on 11/1/17 at 10:56:38 PM Eastern, Q used a particular ciphertext for the first time when signing the post “4, 10, 20.”
In drop #40, on 11/2/17 at 2:18:35 AM Eastern, Q provides a clue to discover the cryptographic key. (Note, I highlight the RARE and stacking signals for the Pepes who were [a lot cooler] up above.)
Using the ciphertext and clue, you can solve the puzzle and conclude Q was using the “A1Z26” cipher to encrypt the information; therefore, the numbers 4, 10, 20 correspond to letters D, J, T (meaning Donald John Trump).
While simple, I believe Q explicitly highlighted this cipher to confirm its use as a valid decode methodology. I also believe Q gave other explicit clues (such as “timestamps have meaning,” “misspellings matter,” and “future proves past”), to help Anons discover other cryptographic keys (such as “deltas”).
To state that differently, I believe valid decode methodologies are sourced from within the Q drops themselves.
To help solidify the understanding of codes and ciphers, and to have a little fun before turning up the heat, let’s look at the famous Ovaltine scene in “A Christmas Story.”
Studying the ciphertext (numbers), cryptographic key (number-to-letter translator), and encrypted message (letters), you’ll find that the cipher used in the film is similar to the A1Z26 cipher, but different in how it maps the alphabet to numbers.
Case Studies in History
Now let’s add some structure.
The following section will chronologically review, at a high level several case studies that contain the use of ciphers and codes, specifically in the context of information warfare.
Again, it’s important to understand the following about their use:
Case Study 1: Parables of Jesus
In the Bible, Jesus uses parables as relatable metaphors to help communicate heavenly things to earthly beings.
In the following verses, Jesus is asked about His use of parables:
Jesus delineates two groups of people—Those around Him and His disciples, who could see His message within the parables), and those who are outside, who could not.
In the following verses, more detail is given:
Jesus indicates that He intentionally uses parables knowing “those around Him and His disciples” will understand, and “those who are outside” will not. He knows the former has the key to unlock His message.
To state that differently, Jesus indicates that the parables are cryptographic puzzles solved by having a relationship with Him.
(Note, there are other cryptographic keys in the Bible, such as faith, prayer, worship. Find out what you can unlock!)
Being the Word (the Logos) of God, and the Truth, everything about Jesus is information warfare.
If “those who are outside” would have understood His message at the time, they would have moved more quickly to persecute and kill Jesus in attempts to stop Him. Therefore, Jesus uses parables as a form of memetic warfare to simultaneously grow His network, propagate His message, and protect His network from attackers. Think of them like Biblical Q drops.
Case Study 2: Cipher of Mary Queen of Scots
With centralization comes trust issues. This is frequently demonstrated by politics and actions affecting one’s ability to project and scale real world physical power (such as a king commanding an army).
Let me ask, if you were a Queen in the 1500s, how would you securely communicate with allies to ensure enemies would not gain an advantage able to usurp your power (right or wrong)? Who could you trust with secrets vital to national security? In what ways would you be spied on? What tools would be available to help you accomplish your mission?
“In 1586, Mary, Queen of Scots, was held prisoner” by "a Protestant loyal to Elizabeth I.”
“Mary’s contact with the outside world was limited to correspondence encrypted by her cipher secretary” … “and smuggled out in casks of ale.”
“Letters between Mary and her allies in England and abroad were painstakingly deciphered and copied.”
“Letters were then carefully re-sealed and sent on to their intended recipients.”
The following illustrates a portion of the ciphers used by Mary:
Case Study 3: The Culper Code Book of George Washington
One of my personal favorites, and my primary inspiration for this article is the information warfare strategy used by Washington during the first American revolution.
“As General Washington struggled to win a war with an army that was perpetually undermanned, undertrained and undersupplied, he relied increasingly on his unseen weapon: a secret intelligence network.”
“The story of Washington’s underground spy network, and how it helped Americans win their revolution, is replete with intrigue: letters written in invisible ink; a rare female agent who went by the mysterious moniker Agent 355; the gruesome execution of the spy Nathan Hale.”
It’s important to recognize that Washington and those fighting on his side were insurrectionists inside of British colonies—traitors to the crown. While they had unique geographical advantages against the King, the threat of being discovered and punished within the colonies by loyalists was lurking around every corner.
“In mid-September 1776, the American officer Nathan Hale was hanged without trial in New York City.”
“Hale’s death illustrated the grave dangers inherent in spying for the rebels.”
The following illustrates a portion of the Culper Code Book:
I extracted the English Alphabet and Base 10 Digits to Culper Code ciphers as an additional example for you to compare against previous ciphers mentioned:
For fun, I also extracted words having three numbers consisting of digits 1, 3, and 5, to illustrate how Washington mapped hundreds of unique words to numbers. Pepes will appreciate the signal.
Case Study 4: The Enigma Machine
Humanity is at a point in history that Lt. General Steven Kwast referred to on Rugpull Radio as a transition from the Industrial Age to the Network Age. This wouldn’t be possible without the following building blocks:
Case Study 5: World War II
Another personal favorite, and my secondary inspiration for this article, is the information warfare strategy used by the US Marines during World War II. I love how it clearly demonstrates how entire languages can be leveraged by militaries to win a contest of power projection:
Conclusion
OK, so how do I plan to tie this all together, and what does it have to do with Covfefe?
Well, remember that Q gave us a key in drops #5 and #6? A cryptographic key, perhaps?
To follow the money, we must first ask, “what is money?”
An honest and holistic search for that answer will unlock the knowledge that the central control of currency (fiat) and money (gold) is the root cause of all sorts of evil. The effects have plagued humanity for millennia. To correct the issue with lasting efficacy, we must eliminate the root cause.
But how?
Alright Covfefe, it’s your time to shine!
Recall, my earlier question: Is Covfefe a cryptographic key, and if so, what information does it allow access to, or what puzzle does it solve?
Referencing the handful of resources, 75 episodes of Rugpull Radio, and other posts across our channels, GMONEY and I have presented a substantial amount of data that strongly suggests Covfefe is both cipher text and a cryptographic key.
This dual purpose seems to be useful in unlocking both “static” and “dynamic” information.
What do I mean?
Static: Information to Understand the War (Big Picture)
Dynamic: Information to Discern the War (Rug Sniffer)
First, let’s address the cipher text aspect, covered in the Covfefe dig:
GMONEY uses the A1Z26 cipher as the decode methodology to unlock the “deep meaning” of Covfefe. This results in the number sequence 3, 15, 22, 6, 5, 6, 5.
As illustrated below, additional analysis connects this number sequence with 3/15 (Ides of March), 11/11 (315th day of the year), the fall of Rome, and our current situation.
I refer to this unlocked data as static (such as history, current state, and end state). This static analysis connects the dots between Q, Trump, Bitcoin, Pepe, and JFK.
Lastly, let’s address the cryptographic key aspect:
While the static information unlocked by using the A1Z26 cipher on the ciphertext (Covfefe) is massive, the numbers themselves also seem to be a cryptographic key themselves—a key that can be used to unlock additional “deep meaning” in a dynamic sense.
What do I mean?
Well, strangely enough, it seems the number sequence derived above is a signal or frequency useful for transmitting information.
To state that differently, it seems the number sequence is a repeating number pattern that has been used to mark a subset of data (such as timestamps, dates and key figures). This subset of data, when compiled and analyzed holistically, is helpful in discerning the fog of war. I refer to this unlocked data as dynamic (such as information relative to current psyops, the transition to a new warfighting domain and narrative warfare).
This dynamic analysis provides key information relative to the digital (bit) counterinsurgency (COIN).
While this topic may seem strange, recognize we are at war; therefore, the use of ciphers and codes is entirely expected. Also, recognize that we are in an irregular and asymmetrical 5th Generation war; therefore, the sources and methods of information control and dissemination are understandably irregular and totally misunderstood.
Remember, “all warfare is based on deception.”
I will finish the discussion with the following graphic, emphasize a few key points, and leave you with several questions to ponder.
I’ll emphasize:
Q states in drop #1127 that communications methods are intentionally different for national security purposes.
Major Jason Lowery discusses a transition to a new war-fighting domain (space) and the national strategic significance of Bitcoin relating to Softwar.
Q states in drop #1002 that “symbolism will be their downfall,” and the NSA is “the BITE that has no CURE.”
Some questions to ponder:
What did Q mean when they said [symbolism] will be their downfall?
Maybe [cryptographic keys] will be their downfall?
Maybe [ciphers] and [codes] will be their downfall?
Have we truly figured out the “true meaning of Covfefe?”
If so, wouldn’t understanding the language make us Keksitani Code Talkers?
Shadilay!
Badlands Media articles and features represent the opinions of the contributing authors and do not necessarily represent the views of Badlands Media itself.
If you enjoyed this contribution to Badlands Media, please consider checking out more of PiP’s work for free on Substack.
Badlands Media will always put out our content for free, but you can support us by becoming a paid subscriber to this newsletter. Help our collective of citizen journalists take back the narrative from the MSM. We are the news now.
























BOOOM
If I could share photos here, I would. Through this technology suggested by Tesla, Trump was able to disassemble the 5G towers. It's the periodic table of the elements. CO V Fe Fe Together they are magnets that essentially cleanse the atmosphere of harmful 5G.